A joint operation by the FBI and the law enforcement agencies of 19 other countries has led to the takedown of the notorious discussion forum for criminal hackers, Darkode.me. It was the most central English-speaking hub for the sale of credit card numbers, criminal hacking hardware, and malware written for commercial sale. Originally called Darkode.com, the forum had shifted several times in response to pressure from authorities and the “white hat” hacking community, adding layers upon layers of security.
It was a highly encrypted, invite-only forum hosted by true paranoiacs, and featuring a tiered access system designed to keep any unavoidable infiltrators away from the most sensitive discussions. With an air of true satisfaction, the FBI announcement makes the implication clear as day: if we can get Darkode, we can get anybody.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Darkode
Via Gust MEES



 Your new post is loading...
Your new post is loading...

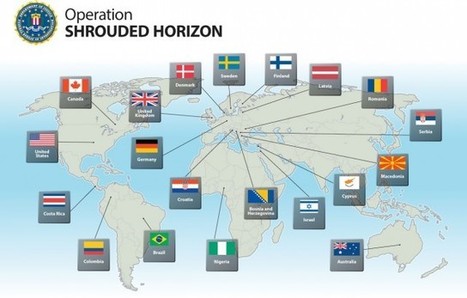







A joint operation by the FBI and the law enforcement agencies of 19 other countries has led to the takedown of the notorious discussion forum for criminal hackers, Darkode.me. It was the most central English-speaking hub for the sale of credit card numbers, criminal hacking hardware, and malware written for commercial sale. Originally called Darkode.com, the forum had shifted several times in response to pressure from authorities and the “white hat” hacking community, adding layers upon layers of security.
It was a highly encrypted, invite-only forum hosted by true paranoiacs, and featuring a tiered access system designed to keep any unavoidable infiltrators away from the most sensitive discussions. With an air of true satisfaction, the FBI announcement makes the implication clear as day: if we can get Darkode, we can get anybody.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Darkode